Visionapp Network Level Authentication
Posted By admin On 08.01.21I've tried enabling/disabling NLA and CredSSP individually and together, no change. If we remove credentials altogether, we get the standard 'Windows authentication' login box, but it looks like the remote server detects the RDM credential as an intermediate party and treats it as a 'saved' password (even if the password was provided interactively), and throws the authentication. Visionapp Remote Desktop 2009 (vRD 2009) is a powerful tool for managing and accessing multiple servers and desktops. VRD 2009 features unparalleled ease of use, accelerated remote desktop access to servers and workstations, detailed logging features, and a new interface that allows administrators to view all connected machines simultaneously.
VisionApp - we care for your eyes. Information Technology and Services Murcia, Murcia 271 followers We provide parents and eye care professionals with apps and technology to care for the eyes. Simple, Efficient and Cost-Effective Remote Access and Administration. Increasing complexities of remote work, cloud adoption and system migration demands simple, efficient and cost-effective remote access for IT professionals and teams. ASG uses cookies and similar technologies to analyze traffic, measure effectiveness, and to personalize your site experience. For more information or to adjust cookie preferences, view our Cookie Policy.By clicking “Accept” you consent to the standard use of cookies. . Configure Network Level Authentication 1. In the navigation pane, locate and then click the following registry subkey: HKEYLOCALMACHINESYSTEMCurrentControlSetControlLsa 3. In the details pane, right-click Security Packages, and then click Modify. In the Value data box, type tspkg.
Recently there has been a lot of attention given to the Remote Desktop Protocol for attacker. The protocol has seen a work in 2011 that abused week passwords and it’s features to copy files and infect other machines and now in 2012 there is a remote code execution bug in the protocol it self. Since the days of Vista and Windows 2008 Microsoft has provided a new mechanism for securing RDP connections with what they call Network Level Authentication, this uses Microsoft CredSSP Protocol to authenticate and negotiate credential type before handing off the connection to RDP Service.
CredSSP first establishes an encrypted channel between the client and the target server by using Transport Layer Security (TLS). Using the TLS connection as an encrypted channel; it does not rely on the client/server authentication services that are available in TLS but does uses it for validating identity. The CredSSP Protocol then uses the Simple and Protected Generic Security Service Application Program Interface Negotiation Mechanism (SPNEGO) Protocol Extensions to negotiate a Generic Security Services (GSS) mechanism that performs mutual authentication and GSS confidentiality services to securely bind to the TLS channel and encrypt the credentials for the target server. It should be noted that all GSS security tokens are sent over the encrypted TLS channel. This tokens can be NTL, Kerberos or PKI Authentication for SmartCards.
The graphic bellow illustrates how this is done:
Most brut force tools currently out there do not take in to account NLA, it would slow down the process even more and add another level of complexity. Since no packet will reach the RDP service until CredSSP has finished negotiation of the connection it protects the servers from DoS and exploits.
NLA is present in the latest versions of Windows, for Server:
- Windows 2008
- Windows 2008 R2
- Windows 7
- Windows Vista
On the client side:
- Windows XP SP3
- Windows Vista
- Windows 7
- Windows 2008
- Windows 2008 R2
- Remote Desktop Connection for Mac
NLA was introduced first with RDP 6.0 in Windows Vista and later on Windows XP SP3.
One of the biggest advantages also is that since TLS is used it will warn us if it can not validate the identity of the host we are connecting to. For this we will need a PKI infrastructure integrated with AD in our Windows environment. On a Windows 2008 environment we can install on a server the role of Active Directory Certificate Service to install a Enterprise CA accepting all defaults so it can provide Computer Certificates to the machines in the domain in an automated way using Group Policy.
Configuring a GPO for NLA
In this example I will show how to configure a GPO for issuing a Certificate to each host in the Domain and Configure NLA authentication for RDP. In a production environment you may wish to separate these or keep them in one policy depending on your AD design.
Lets start by selecting from Administrative Tools the Group Policy Management tool:
On the tool we create a New Group Policy Object:
We give this policy a Name:
Once created we edit this policy by right clicking on it an selecting Edit:
Now we select Computer Configuration/Policies/Windows Settings/Public Key Policies/Automatic Certificate Request Settings:
We now right click on Automatic Certificate Request Setting and select to create a new Automatic Certificate Request, this will request to the CA a new Computer Certificate and renew the certificate when it expires automatically.
When the wizard starts we click Next then we select Computer Certificate Template:
We click on Next and then on Finish. Now we select Computer Configuration/Policies/Windows Settings/Public Key Policies under that node we double click on Certificate Services Client – Auto-Enrollment we now select on the properties under Configuration Model we select Enable and make sure that the boxes for managing certificates in the store and for updating the certificate if the template is modified.
Now we have finished the section that will cover the certificate assignment for computers that get this GPO applied to.
For configuring RDP to use NLA we now go to Computer Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Settings/Remote Desktop Session Host/Security
Select Require user authentication for remote connections by using Network Level Authentication and double click on it. On the properties screen select Enable and click on OK.
Now lets configure the client settings to make sure that we always select to warn in the case the host certificate con not be authenticated. We select Computer Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Settings/Remote Desktop Connection Client
We double click on Configure Authentication for Client
Select Enable and set the Option to Warn me if authentication fails
Click on OK and close the screen. Know you should have a proper policy that cam be applied, but before we apply the policy we have to give permission on the Domain Computers group in the domain the permission to apply it:
And now we have a GPO that can be linked to any Domain in the forest or Organization Unit. Once applied when a connection is made we can see the security in use by clicking on the lock on the top of a Remote Desktop Session in Windows and it will tell us how we where authenticated:
On those host that do not have RDP enabled you will see that the only option available is to use NLA
As always I hope you find this blog post informative and useful.
While working on domain-controlled systems, upon trying to remotely access computers, users have reported the following error:
“The remote computer that you are trying to connect to requires network level authentication (NLA), but your windows domain controller cannot be contacted to perform NLA. If you are an administrator on the remote computer, you can disable NLA by using the options on the remote tab of the System Properties dialog box.”
Cause
The crux of the error suggests that the domain controller cannot be contacted, thus network level authentication cannot be performed. The error has been reported even when Network Level Authentication was enabled.
Our strategy towards dealing with the issue would be to totally disable Network Level Authentication. While the NLA provides extra security, we perhaps have no choice here.
Solution 1] – Delete Default.rdp file
1. Go to My documents and if you find a file named Default.rdp , just delete it. Try again.
If it does not work , Remove the machine from the domain then add it again. Now, check if the problem persists.
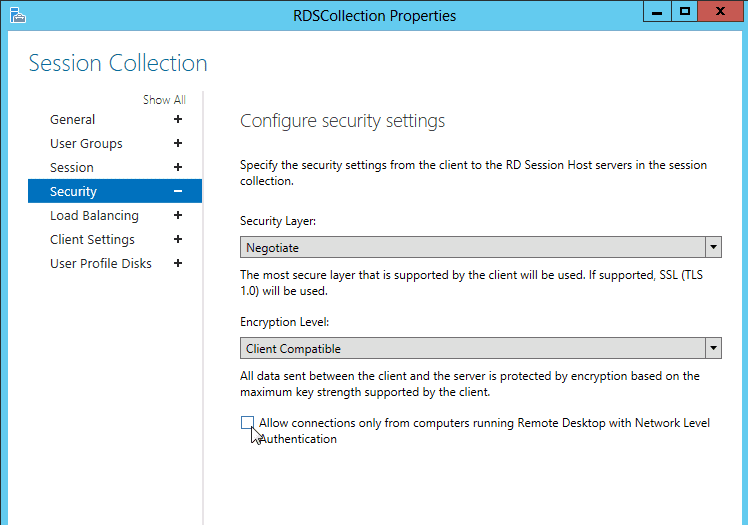
Solution 2] Disable NLA using Properties
1] Press Win + R to open the Run window and type the command sysdm.cpl. Press Enter to open the System Properties window.
2] In the Remote tab, uncheck the option for “Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended).”
3] Click on Apply and then OK to save the settings.
Solution 3] Disable NLA using Registry
If the above method does not work, we can disable NLA from the Registry itself.
1] Press Win + R to open the Run window and type the command regedit. Press Enter to open the Registry Editor.
2] Select File and then click on Connect Network Registry.
Connect to the network Device by entering details.Wait till the network connects.
3] Navigate to the following path:
- HKLM
- SYSTEM
- CurrentControlSet
- Control
- Terminal Server
- WinStations
- RDP-Tcp
4] Change the values of the entries SecurityLayer and UserAuthentication to 0.
5] Close the Registry Editor.
6] Restart the system.
Solution 4] Disable NLA using Powershell
1] Press Win + R to open the Run window and type the command PowerShell. Press Enter to open the Powershell window.
2] Copy-paste the following command in Powershell:
Hit Enter and then enter command below.
3] Press Enter to execute the command and restart the system once done.
Hope it helps!